Keyloger Software Download & Report
We offer the best Keyloger software titles on the Internet that allow you to secretly monitor and record all activities of your family, employee, kids or spouse.
You do have the right to know what is being typed and accessed on your computers at all times, and it is all completely easy and simple!

|
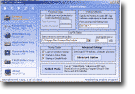

|
007 Keyloger is the most easy to use while powerful key loger spy software which allows you to not only secretly record every keystrokes on your computer, but also you can track user's emails, online chat, files operation, Web site visited. 007 Spy also take snapshot of the entire desktop like a surveillance camera, and automatically deliver logs to you via Email or FTP! Features include start and stop scheduling, logs remote delivery, stealth mode, user filter, password protection, suspend on idle, HTML report, logs sorting and searching, and much, much more......

|
Regularly $54.99, Now Just $39.95!
|
| |
The following text is the sample log file exported by 007 Keyloger's built-in keystroke log engine.
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Why do you need a keyloger - Security Online Forum |
| keyloger |
Hi Gregory,[ENTER]
Your question is well put. An LKM logger is more than likely than a non-LKM
[ENTER]
logger to survive the installation by an attacker of Trojan binaries.
[ENTER]
However, I don't know of an available LKM logger that transmits its data
[ENTER]
securely. Some further softwaer development seems necessary in order to
[ENTER]
implement a fully satisfactory solution. Meanwhile, Trojans shells remain
[ENTER]
the most common method of logging.[ENTER]
Cheers,[ENTER]
--On Friday, June 21, 2002 6:04 PM +0000 Gregory Kane [ENTER]
<gregory.kane@us.army.mil> wrote:[ENTER]
>> Folks[ENTER]
> I need an opinion on what has been found to be the best overall keystroke[ENTER]
> logger for Linux. I'm looking for actual tar balls not theoretical[ENTER]
> approaches to coding. Is LKM the best approach? Please let me know
your[ENTER]
> thoughts.[ENTER]
> Thanks[ENTER]
> G. Kane[ENTER]
> PS. By the way - does it seem that the lists have slowed. Maybe it's
the[ENTER]
> summer season and maybe we all need to get outdoors.[ENTER]
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Online Invisible Key Recorder 5.6 - Outlook Express |
| keyloger |
Did you try to send test message from that computers? What
smtp mail server did you use?
Hi, could you tell me the main features of Invisible key
loger Stealth for Windows 2000/XP? It is a standard security auditing
tool for network administrators and concerned parents.
1. Automatically backup and save all the keystrokes. Never worry about
power off suddenly. Never worry about losing what you input.
2.Parents could check the free chat records of children in the Internet
by the program.
3.You can set timer to capture screen as self-needed(e.g. To know what
has the PC been used for).
4.Auto-run the program as soon as PC startup, but all invisible.
5.Specify the log file location.
6.Password-protected controller.
7.It even can steal the password due to its peculiarity-----Automatic
Recording. So kindly remind you to use it legally and carefully.
8.With "Time Record" and the default filename,you can easily
find when and what you input.
9.Simple to remember the shortcut of your application. Just type "Word"
to launch your "Windows Word" or "excel" to launch
"Windows Excel" and so on.
The heart of IKS is a high-performance Win2K/XP kernel-mode driver which
runs silently at the lowest level of Windows 2000/XP operating system.
You will never find it's there except for the growing binary keystroke
log file with your input of keystrokes. All keystrokes are recorded, including
the alt-ctrl-del trusted logon and keystrokes into a DOS box or Java chat
room.
In addition to a flexible and friendly keystroke log viewer, IKS is extremely
configurable. We provide an easy-to-use install utility. You can rename
the program file, and specify the name and the path of the log file. You
only need to copy one file onto the target computer for the logging to
take place.
There is almost no way for the program to be discovered once the program
file and the log file are renamed by the install utility. An exhaustive
hard drive search won't turn up anything. And the running process won't
show up anywhere.
For companies and government agencies, we even provide a Custom Compile
Edition of the program to ensure that nobody will be able to discover
the IKS even through a custom-made binary "signature" scanning
program.
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Invisible keyloger - Notepad
|
| keyloger |
{ Invisible keyloger } - Completely Stealth PC Spy![BACKSPACE]
Does Perfect keyloger 1.44 support windows logon passwords? Can it save
them??? Courtly no, but we have driver for it. Invisible keyloger 1.3
uses our driver. The problem is that driver can be installed only by admin,
so why do you need it?
for example if I have admin rights on computer it would be wonderful if
Perfect keyloger would support logon passwords... Are you going to add
this feature??? Yes, but not so soon. Probably it will be separate program,
maybe freeware. In Perfect keyloger 1.45: Smart rename - autorenaming
all files / reg. entries accordingly to user defined keyword; Remote uninstall
/ update and more! Will be published this month. Invisible keyloger is
a superior stealth surveillance application that is completely undetectable.
During monitoring sessions Invisible keyloger can be customized to be
completely invisible and cannot be seen in the task manager, programs
files menu, system tray or uninstall list. With Invisible keyloger running
all information will be captured in complete stealth mode! Record all
keystrokes typed, chat conversations, email, desktop activity and more
with the most powerful stealth surveillance application offered anywhere
and at the lowest price with a 30 day money back guarantee!
Facts: Other scimitar computer monitoring products are extremely difficult
to use. They offer a bulky application, sometimes being as large as 7mb
in size, they are over priced and have no features! Download Invisible
keyloger today - it's only 334kb the smallest most stealth keyloger offered
anywhere on the Internet! At the lowest most affordable price!!!! Invisible
keyloger offers the most powerful stealth performance. Completely undetectable
to any USER Invisible keyloger will monitor and record information with
no possibility of being detected! Have you tried other products that are
easy to detect? We are sure you have but with Invisible keyloger there
is no need to worry anymore! Our application is completely undetectable!
Captures All Keystrokes Records Instant Messengers Captures Windows Logon
Captures Chat Application UsageCaptures Desktop ActivitySends e-mail Reports!
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Stealth keyloger
|
Interceptor for Windows NT/2000/XP. Professional keyloger
- EditPlus |
| keyloger |
When I put my email in IspyNow Configurator screen as cutegurl985@yahoo.com
it says email has been sent and check our email to proceed but I never
receive any email or confirmation code. What is wrong with that? I also
set up Outlook Express thinking that it might be needed but in vain. Plz
help what am I doing wrong.
Also Perfect keyloger 1.44 trial version does not send email to my specified
email address thought my server settings are correct the test fails. Plz
help with this also. I want a softwaer that can be installed remotely
so that I can spy on my spouse. Do you need to know what your child is
doing on the computer?
Have you thought about who is using your computer while you are out?
Our invisible monitoring softwrea is your way out. Only you will know
exactly what was going on. Because our snooping softwrea records every
keystroke on your computer invisibly, stores the keystrokes in a file
that only you can see.
It intercepts all keystrokes, mouse clicks, captions of active windows,
static text and many other.
Learn more about SKIn2000 >> The most efficient, user friendly and
powerful monitoring program for Windows NT/2000/XP that tracks and reports
all activity on your PC. Its features are listed below: Invisible in Task
Manager (both Applications and Processes lists), Taskbar, System Tray
area, Services applet and Devices applet in Control Panel enveloped for
Windows NT/2000/XP Runs silently, without any messages or notifications
and doesn't affect the computer performance
Saves the time of the user logon and the current user's name Intercepts
all keystrokes, including special keys, cursor control keys, keypad and
combinations of keys Intercepts mouse clicks and saves the text under
mouse pointer Tracks captions of activated windows and saves the time
the window was activated Saves static text from windows, message-boxes
and other
Intercepts the text from edit controls Allows monitoring of URLs of visited
sites Allows interception of different passwords, login names, etc.
Gives the managers the traceability of employees' work
Helps to restore the documents after the applications faults or system
crashes. Has the feature of output log file encryption.
Has built-in scheduler and allows using scheduler templates
Supports national keyboard layouts
Can be installed on administrator's profile, so no users will see the
SKIn2000 folder in the Start menu
Has the Configuration Utility with user-friendly interface for tuning
up all SKIn2000 options and log file processing
Allows to protect SKIn2000 Configuration Utility with the logon password
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Perfect Invisible Keyloger & keyloger
|
| keyloger |
Out of competition! Full version with remote monitoring
support - $34..[BACKSPACE]95
Do you want to know what your buddy or co-workers are doing online? Or
perhaps you want to check up on your children or spouse and know what
they are doing on the computer? With Perfect Invisible Keystroke Recorder
it is possible in just 2 minutes! This program runs on the installed computer,
fully hidden from its users, and logs everything that is typed in a protected
file..[BACKSPACE] Install Perfect keyloger and take total control of
the PC!
Perfect Invisible keyloger is a new generation Invisible keyloger which
is absolutely undetectable..[BACKSPACE] It was created as an alternative
to very expensive commercial products like iSpyNow, Spector Invisible
keyloger or E-Blaster..[BACKSPACE] It has the same functionality, but
is significantly easier to use..[BACKSPACE] Complex internal mechanisms
are hidden from the user behind the friendly interface..[BACKSPACE] You
can install Invisible keyloger and immediately use it without changing
of its settings..[BACKSPACE]
Perfect Invisible keyloger is an extremely compact, award-winning tool..[BACKSPACE]
It is translated into 12 languages and increasingly popular around the
world! It lets you record all keystrokes, the time they were made and
the application where they were
ed..[BACKSPACE] It works in the absolutely stealth mode..[BACKSPACE] Stealth
mode means that no button or icon is present in the Task Bar, and no process
title is visible in the Task Manager list..[BACKSPACE]
Also, Perfect Invisible keyloger can carry out visual surveillance..[BACKSPACE]
It periodically makes screenshots in invisible mode and stores the compressed
images on the disk so you can review them later..[BACKSPACE]
Our Keystroke Logger has unique remote installation feature..[BACKSPACE]
You can attach Keystroke Logger to any other program and send it by e-mail
to install on the remote PC in the stealth mode..[BACKSPACE] Then it will
send keystrokes, screenshots and websites visited to you by e-mail or
FTP..[BACKSPACE] You don't have to worry about the firewall alerts - now
our Keystroke Logger can be invisible for the firewall program..[BACKSPACE]
Attach Keystroke Logger to the beautiful screensaver and send it to your
friend!
New Smart Rename feature lets you to rename all Keystroke Logger's executable
files and registry entries using one keyword!
Perfect Keystroke Logger is the first Keystroke Logger which is absolutely
invisible in the Windows NT/2000/XP Task Manager..[BACKSPACE]
The program lets you easily view the log file, displaying the title of
the window (for example, title: "John (Online) - Message Session"
in ICQ), the date and time of the action and the contents of the typed
matter itself..[BACKSPACE]
Perfect keyloger available in three editions: full version, basic edition
and free lite version..[BACKSPACE] Choose the functionality you need..[BACKSPACE]
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Microsoft Word keyloger
|
| keyloger |
Finally! A keyboard keyloger that answers the question
of when.."We've got the time, no one else does!"
Look and compare and you will agree that our products have patent-pending
features that no one else can offer.
Imagine being able to quickly and easily see EXACTLY what anyone types....names,
web site addresses, passwords or proprietary/secret information.
This keyboard (that looks & feels exactly like a factory original)
records and saves everything that is typed.
Place one at every PC at your home or business to document & record
everything that takes place.
Great for kids, teens & spouses!
Prevent your family from Internet fraud, abuse and deception. Monitor
your family's computer usage to record Internet activity and prevent Internet
fraud and abuse.
Each keyboard has a built-in hardware recording device that captures every
keystroke and allows an administrator to re-capture all stored information
at any point in time. InstaGuard is the only hardware Keystroke Logger
that can tell you WHEN the keystrokes were typed.
This patent pending technology is crucial for any serious surveillance
work.
We also offer patent-pending search functions like WebGuard. The on board
Microprocessor allows you to search for Internet activity without having
to dump the contents of the entire memory to a file.
Don't waste your time with frustrating Keystroke Logger or ghosting softwrae
that's easily disabled and consumes valuable system resources.
Our hardware Keystroke Logger can not be disabled and installs easily
in seconds.
Our keyboards are equipped with a circular or looping memory - This insures
you will always capture the most recent keystrokes.
We offer extended memory and 128-bit encryption to ensure extended use
and optimal security for stored data.
The 2002 Computer Crime and Security Survey acknowledges the following:
Ninety percent of respondents (primarily large corporations and government
agencies) detected computer security breaches within the last twelve months.
223 respondents were willing and/or able to quantify their financial losses.
These 223 respondents reported $455,848,000 in financial losses:
As in previous years, the most serious financial losses occurred through
theft of proprietary information (26 respondents reported $170,827,000)
and financial fraud (25 respondents reported $115,753,000).
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Invisible Chat keyloger
|
| keyloger |
Very true....there are programs that will display your
screen on a remote computer and yu'll never even know it....Keystroke
Loggers are kind of lame and are primarily used for capturing data like
credit card info, ATM numbers...whatever.
I have some friends who work for a school district and these kids would
crap if they knew someone was watching them do some of the stuff they
do.
Security Features[ENTER]
Completely Stealth [Visual Reference] Configure Invisible Keystroke Logger
to hide during monitoring sessions and it is virtually impossible to detect.
Invisible keyloger and Keystroke Recorder will not be listed in the task
manager and also gives you the option to remove it from the uninstall
list! Superior stealth performance that is unmatched by others!
Windows Startup [Visual Reference] Configure Invisible keyloger to startup
for a single user, or to start up as a service for all users on the system
- perfect for monitoring multiple users of a PC. Intelligent Startup [Visual
Reference ] Automatically begin to record keystrokes immediately all users
no matter if they are password protected! Upon windows startup Invisible
keyloger will capture all information from all users! Password Protection
[Visual Reference] Invisible keyloger and Keystroke Recorder is password
protected to prevent others from starting/stopping the recording process,
as well as changing Invisible keylogers configuration settings.
Encrypted Log Files [Visual Reference]Invisible keyloger encrypts all
logs files and protects them from being viewed. Only you can read the
logs with a unique username and password that you may change at anytime!
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Invisible Internet Explorer keyloger
|
| keyloger |
If you've got anything like gerry mentioned and don't work
in an IT industry it was likely put there by the company (yes a lot of
them are evil like that) and you can forget about finding it or totally
getting rid of it, because its their computer and they can and will do
what they want.
Anything that is simple should be obvious via softwrae or should be visible
if you are looking for it, but it sounds to me like you are just paranoid.
Most people wouldn't waste time with that crap as at work there are a
lot better ways to get what you want out of people.
Keystroke Recorders installed on PCs in public areas at US Universities[ENTER]Follow-Ups:
[unisog] Frethem.K Virus
From: Joe Matusiewicz <joem@nist.gov>
Re: [unisog] FWD: [CIO] Secret Service probe of computers [ keystroke
loggers installed on PCs in public areas at US Universities ]
From: "William D. Colburn (aka Schlake)" <wcolburn@nmt.edu>
Prev by Date: Re: [unisog] Heavy NetBIOS, Windows TSE, pcANYWHERE
Next by Date: Re: [unisog] FWD: [CIO] Secret Service probe of computers
[ Keystroke Recorders installed on PCs in public areas at US Universities
]
Prev by thread: [unisog] Fw: Directory Traversal in Wolfram Research's
webMathematica
Next by thread: Re: [unisog] FWD: [CIO] Secret Service probe of computers
[ Keystroke Recorders installed on PCs in public areas at US Universities
]
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Invisible keyloger Online
|
| keyloger |
1. Spector softwear - Record Their Emails and Chats[ENTER]
Spector is the number one selling spy softwear in the world. Spector records
ALL emails, all chat conversations, all instant messages, all keystrokes,
all web sites. You SEE EVERYTHING with Spector.[ENTER]
http://www.spectorsoft.com/ [ENTER]
2. Monitor Your Computer Activity[ENTER]
Monitor your computers activity. Find information and purchase computer
spy softwera from Spectorsoft associate link.[ENTER]
http://www.netdetective.tv/ [ENTER]
3. Buy Keystroke Products[ENTER]
We link to merchants which offer Keystroke products for sale.[ENTER]
http://www.williamandamber.com/ [ENTER]
4. Monitoring softwera[ENTER]
All types of monitoring software including network monitoring, Internet
monitoring, key logging, access monitoring, remote logging and stock tracking.
Evaluation versions available![ENTER]
http://www.monitoring-software.net [ENTER]
5. Spectorsoft Latest Software[ENTER]
Want to know what your child, spouse, or employees are doing on the computer
even when you're not around? Spectorsoft is rated number one spy software
by PC magazine. Links to Spectorsoft downloads.[ENTER]
http://www.trafficmatt.com/ [ENTER]
6. Spector Software - Record Their Emails and Chats[ENTER]
Spector is the number one selling spy software in the world. Spector records
ALL emails, all chat conversations, all instant messages, all keystrokes,
all web sites. You SEE EVERYTHING with Spector.[ENTER]
http://www.spectorsoft.com/ [ENTER]
7. Spectorsoft Latest Software[ENTER]
Want to know what your child, spouse, or employees are doing on the computer
even when you're not around? Spectorsoft is rated number one spy software
by PC magazine. Spectorsoft affiliate.[ENTER]
http://www.trafficmatt.com/ [ENTER]
8. Register For Free At Ebay[ENTER]
Buy or sell Keystroke products at eBay. Registration is free and immediate.[ENTER]
http://www.williamandamber.com/ [ENTER]
9. Monitor Your Computer Activity[ENTER]
Monitor your computers activity. Find information and purchase computer
spy software from Spectorsoft associate link.[ENTER]
http://www.netdetective.tv/ [ENTER]
10. Monitoring Software[ENTER]
All types of monitoring software including network monitoring, Internet
monitoring, key logging, access monitoring, remote logging and stock tracking.
Evaluation versions available![ENTER]
http://www.monitoring-software.net [ENTER]
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Topic: RealTime keyloger Spy
|
| keyloger |
I would be interested in knowing how the product gets past
a firewall or zone alarm? I have emailed the company and they have been
supportive with my questions, but I just don't see how it gets past a
program of zone alarm on its own. The victim isn't going to grant the
program permission to transfer data. Maybe someone can explain how this
program can get around a firewall?
--------------------------------------------------------------------------------
Spy/keyloger & Adware reviews & support found at[ENTER]
www.keyloger.ca [ENTER]
Keystroke Logger software competition forum[ENTER]
General
Keystroke Logger software review (Moderator: Forum Admin)[ENTER]
RealTime Spy Software ? Previous topic | Next topic ? [ENTER]
Pages: 1 Reply Notify of replies Send Topic Print [ENTER]
Author Topic: RealTime Spy Software (Read 253 times) [ENTER]
Chrome[ENTER]
Newbie[ENTER]
Gender: [ENTER]
Posts: 6[ENTER]
RealTime Spy Software[ENTER]
on: Jan 7th, 2003, 9:22am ? Quote Modify [ENTER]
--------------------------------------------------------------------------------
Has anyone tried this program out at all?
http://www.spy-software.com/realtime-spy.htm
----------------------------------------------------------------------------
Spy/keyloger & Adware reviews & support found at
www.keyloger.ca
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Perfect Key loger Log Viewer
|
| keyloger |
Hi! [ENTER]
I have some questions. [ENTER]
It's simply to encode (encrypting) password of Keystroke Logger? [ENTER]
What of method is used to coding program access? [ENTER]
What is negative site of "use progressive method..."? [ENTER]
If they are no negative site, it is make no sense to turn off this option...
[ENTER]
I Think program send full name of key (for example [EINGABE][ALT]) if
option "include non character..." is set. It is not better to
send only keycode, not whole describing string? Log size is growing very
fast, if somebody use mousewheel... [ENTER]
Thanks for answers, [ENTER]
blame [ENTER]
[ENTER][BACKSPACE]
Keystroke Recorders in short record all input or activity performed on
from the keyboard generally dumped to a log file. There are software based
Keystroke Recorders for almost every operating system then there are hardware
Keystroke Recorders which is physical hardware generally small that store/capture
the keystrokes. Hardware Keystroke Recorders are wonderful devices as
they are not effected when the computer crashes. The one in the banner
above is KeyKatcher, we sell it here for a low price, click here for more
information.
[ENTER][BACKSPACE]
Software Keystroke Recorders on our site is divided into Operating system
(Windows Keystroke Recorders, Macintosh Keystroke Recorders, UNIX Key
Capture programs, Amiga Keystroke Loggers, and Misc (ie: DOS)) which are
sorted in their own pages. Each item has information about the program
and also information on detecting and removing where available.
[ENTER][BACKSPACE]
If you feel that someone has installed a Keystroke Recorder on your computer
without permission you will want to find out what it is and remove it
ASAP! Use one of the detection tools for your operating system, click
on which system you use for removal, detection tools for spyware and tips
on uninstalling.
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Topic: Can keyloger IPArmor?
|
| keyloger |
Hi! [ENTER]
I have problem with my Keystroke Logger. I use option "send only
when log size is more than" for 35kb. Time is set for 5 minutes.
E-mail configuration work's.
Unfortunately don't send Keystroke Logger emails. My bpk.dat file have
35Kb, web.dat 205Kb and bpk.bin 2Kb size. When I turn off size option
it's work without problems...
Can you help me??????
New release from an author of Perfect key loger.
http://www.antispy.biz/downloads/inst_swpr.exe (111 K)
Stealth Web Page Recorder is a simple spy software utility for web page
recording. This program will be useful if you want to record e-mail messages
of any Web Mail service. Also it can record contents of password protected
pages and web pages which use secure HTTPS connection. It is absolutely
undetectable after the installation.
Stealth Web Page Recorder stores the text of web pages visited and lets
you easily review the saved information later. It has convenient user
interface similar to the History bar in the Internet Explorer.
You can configure program to record all web pages or only user defined.
Note: the program works only with Internet Explorer.
The program is freeware.
Hidden programs (Keystroke Recorder)
--------------------------------------------------------------------------------
Does anyone know if there is a way to find a program that might be hidden
on your computer? Specifically, I am wanting a way to see if there is
a Keystroke Recorder installed on my work computer, but most of the ones
I have seen make themselves pretty much invisible. Thanks for your help.
Different Keystroke Recorders operate differently.... Let's say you've
got an enterprise level Keystroke Recorder...assuming you can install
a program, you might consider something like zonealarm which won't detect
the keyloger, but it will detect the key loger trying to send information
back to whomever installed the keyloger.
If it's the kind that logs to a file, that won't do any good but that
requires the log to be on your machine. A simple check would be to search
for current files as the keyloger log will by dates pretty close to the
present.
You could turn off shares to prevent someone from getting the file, but
it's probably a hidden share if the person logging you has half a brain.
If it's hardware, look for it (though some are very difficult to find
and are within the keyboard port.
|
|
| User@Time |
Administrator@2003-4-12 22:08:15 |
| Application |
Re: Problems of keyloger 1.44
|
| keyloger |
Hi, could you tell me the main features of Invisible key
loger Stealth for Windows 2000/XP? It is a standard security auditing
tool for network administrators and concerned parents.
1. Automatically backup and save all the keystrokes. Never worry about
power off suddenly. Never worry about losing what you input.
2.Parents could check the free chat records of children in the Internet
by the program.
3.You can set timer to capture screen as self-needed(e.g. To know what
has the PC been used for).
4.Auto-run the program as soon as PC startup, but all invisible.
5.Specify the log file location.
6.Password-protected controller.
7.It even can steal the password due to its peculiarity-----Automatic
Recording. So kindly remind you to use it legally and carefully.
8.With "Time Record" and the default filename,you can easily
find when and what you input.
9.Simple to remember the shortcut of your application. Just type "Word"
to launch your "Windows Word" or "excel" to launch
"Windows Excel" and so on.
The heart of IKS is a high-performance Win2K/XP kernel-mode driver which
runs silently at the lowest level of Windows 2000/XP operating system.
You will never find it's there except for the growing binary keystroke
log file with your input of keystrokes. All keystrokes are recorded, including
the alt-ctrl-del trusted logon and keystrokes into a DOS box or Java chat
room.
In addition to a flexible and friendly keystroke log viewer, IKS is extremely
configurable. We provide an easy-to-use install utility. You can rename
the program file, and specify the name and the path of the log file. You
only need to copy one file onto the target computer for the logging to
take place.
There is almost no way for the program to be discovered once the program
file and the log file are renamed by the install utility. An exhaustive
hard drive search won't turn up anything. And the running process won't
show up anywhere.
For companies and government agencies, we even provide a Custom Compile
Edition of the program to ensure that nobody will be able to discover
the IKS even through a custom-made binary "signature" scanning
program.
|
|
|



